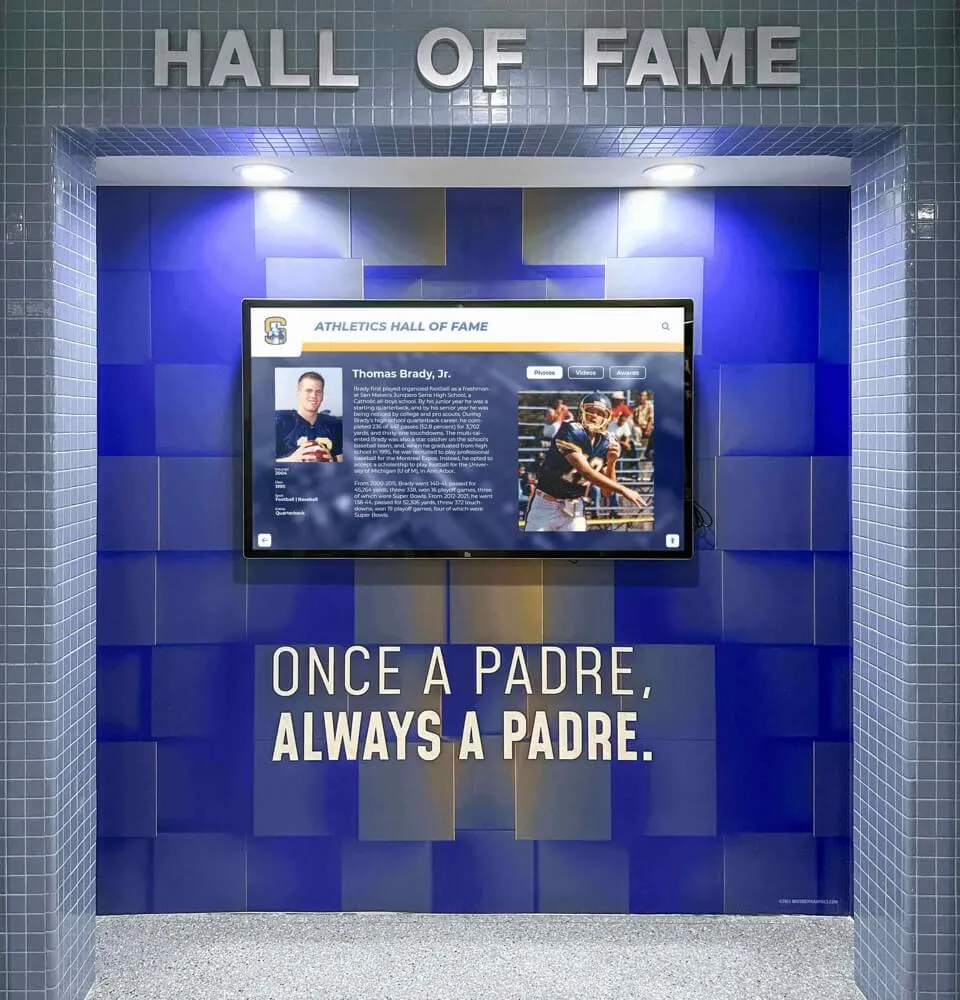
The Security Landscape for Educational Digital Displays
Educational institutions face unique security challenges when implementing digital recognition systems:
- Sensitive Data: Student records, alumni information, and academic achievements require protection
- Public Access: Display systems must balance accessibility with security controls
- Regulatory Compliance: FERPA, GDPR, and state privacy laws impose strict requirements
- Network Integration: Systems connect to school networks containing additional sensitive data
- Physical Security: Public display locations present unique vulnerabilities
Understanding these challenges is the first step toward implementing technically sound and secure digital recognition systems.
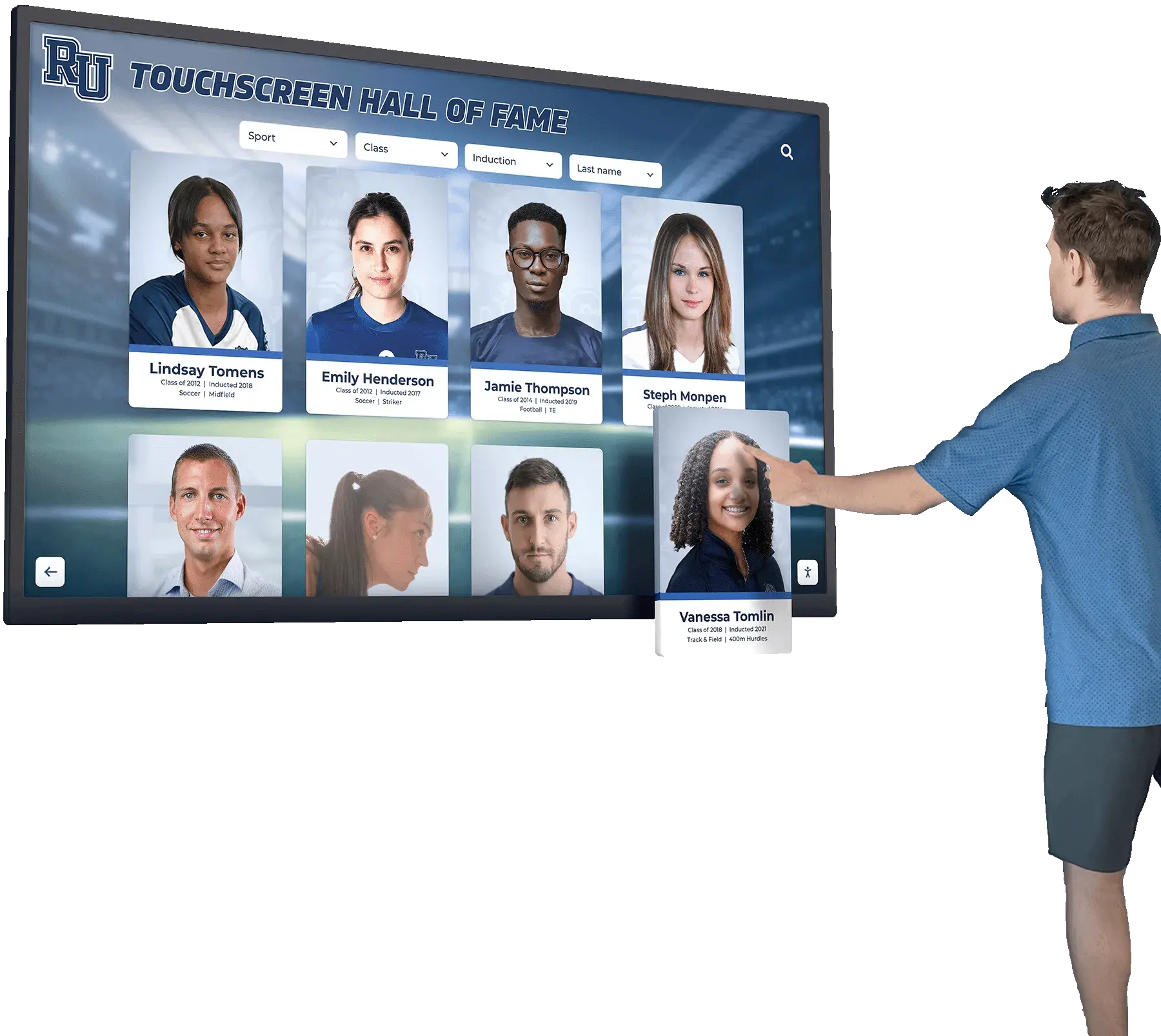
FERPA Compliance for Digital Recognition Systems
🔒 Protected Information
FERPA protects personally identifiable information (PII) including:
- Student names linked to academic records
- Graduation dates and academic honors
- Contact information and addresses
- Photos connected to educational records
- Academic performance data
📋 Directory Information
Schools may publicly display directory information after proper notification:
- Names and recognition titles
- Athletic participation and awards
- Dates of attendance
- Honors and achievements
- Photos from school activities

Essential Security Measures

Multi-Layered Security Approach
These security measures integrate seamlessly with effective content management strategies for optimal protection.
Data Classification and Information Governance
Information Classification Framework
🌍 Public Information
- School name and basic information
- General achievement categories
- Historical milestones
- Public event photos
- Directory information (with consent)
🔐 Restricted Information
- Individual academic records
- Personal contact details
- Detailed achievement descriptions
- Class rankings and GPAs
- Disciplinary records
⚠️ Confidential Information
- Social Security Numbers
- Medical information
- Financial aid records
- Counseling records
- Special education data
Proper classification enables schools to implement appropriate security controls while maintaining engaging alumni engagement features.
Physical Security Considerations
Protecting Digital Displays in Public Spaces
Location Security
- Controlled access areas
- Surveillance camera coverage
- Adequate lighting
- Clear sight lines for monitoring
Hardware Protection
- Tamper-resistant enclosures
- Cable management and protection
- Physical access controls
- Anti-theft mounting systems
Interface Security
- Session timeout controls
- Screen lock mechanisms
- USB port disabling
- Administrative access protection
Power and Network
- Uninterruptible power supplies
- Network segregation
- Secure Wi-Fi connections
- Emergency shutdown procedures
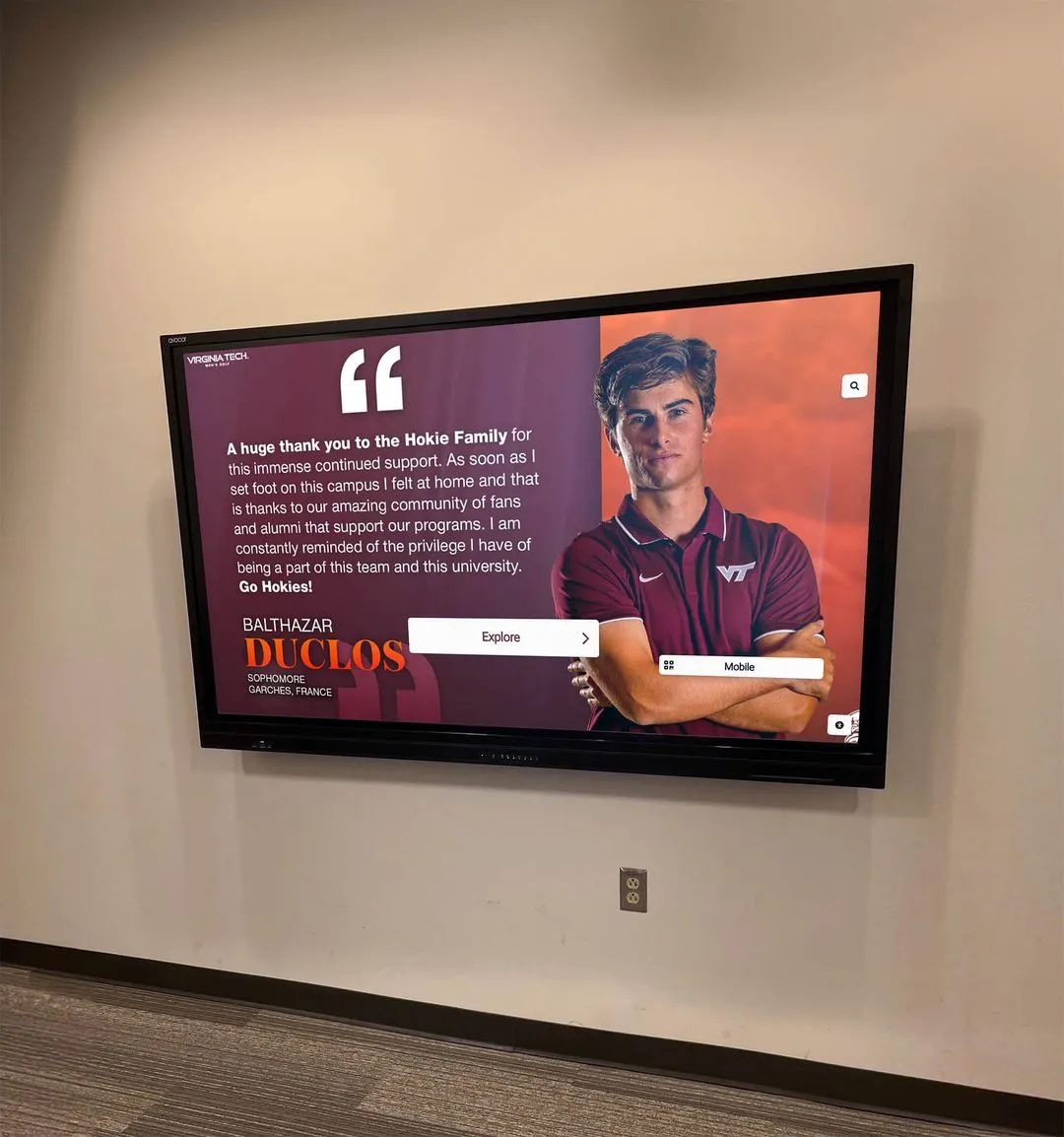
Vendor Security Evaluation
Selecting Security-Conscious Technology Partners
When evaluating digital Wall of Fame vendors, security capabilities should be a primary consideration:
<div class="evaluation-criteria mt-4">
<div class="criteria-item mb-2">
<span class="criteria-badge certification">Certifications</span> SOC 2 Type II, ISO 27001, FERPA compliance documentation
</div>
<div class="criteria-item mb-2">
<span class="criteria-badge experience">Experience</span> Proven track record with educational institutions and regulated industries
</div>
<div class="criteria-item mb-2">
<span class="criteria-badge infrastructure">Infrastructure</span> Cloud security, data center certifications, backup procedures
</div>
<div class="criteria-item mb-2">
<span class="criteria-badge support">Support</span> 24/7 security monitoring, incident response procedures, staff training
</div>
<div class="criteria-item mb-2">
<span class="criteria-badge transparency">Transparency</span> Regular security reports, penetration testing results, compliance audits
</div>
</div>
<p class="mt-3">Thorough vendor evaluation supports successful <a href="/blog/data-migration-digital-wall-of-fame/">data migration projects</a> with security as a priority.</p>
</div>
<div class="col-md-5">
<img src="/images/Wingate-University.webp" alt="Vendor Security Evaluation" class="img-fluid rounded shadow" />
</div>
Incident Response and Recovery Planning
Preparing for Security Incidents
Schools must prepare for potential security incidents with comprehensive response plans:
Response Team Structure
Response Procedures
Regulatory Reporting Requirements
Staff Training and Security Awareness
Building a Security-Conscious Culture
Effective security requires ongoing education and awareness among all staff members who interact with digital recognition systems:
<div class="training-modules mt-4">
<div class="module-item p-3 mb-3">
<h4>📚 Data Privacy Fundamentals (Annual - 2 hours)</h4>
<ul>
<li>FERPA requirements and school policies</li>
<li>Identifying and protecting PII</li>
<li>Proper disclosure procedures</li>
<li>Social engineering awareness</li>
</ul>
</div>
<div class="module-item p-3 mb-3">
<h4>🛠️ System Security Procedures (Quarterly - 1 hour)</h4>
<ul>
<li>Secure login and authentication</li>
<li>Content approval workflows</li>
<li>Incident reporting procedures</li>
<li>Physical security protocols</li>
</ul>
</div>
<div class="module-item p-3 mb-3">
<h4>🚨 Emergency Response Training (Bi-annual - 1 hour)</h4>
<ul>
<li>Recognizing security incidents</li>
<li>Immediate response procedures</li>
<li>Communication protocols</li>
<li>Recovery and documentation</li>
</ul>
</div>
</div>
</div>
<div class="col-md-4">
<img src="/images/NW-Missouri.webp" alt="Security Training Session" class="img-fluid rounded shadow mb-3" />
<div class="training-metrics p-3">
<h4>Training Effectiveness</h4>
<div class="metric-item">
<strong>Completion Rate:</strong> Target 100%
</div>
<div class="metric-item">
<strong>Assessment Scores:</strong> Minimum 85%
</div>
<div class="metric-item">
<strong>Incident Reduction:</strong> 40% fewer security issues
</div>
</div>
</div>
Ongoing Security Monitoring and Maintenance
Continuous Security Management
Maintaining security requires ongoing attention and systematic monitoring:
Automated Monitoring
Regular Assessments
Security Maintenance Calendar
- Log review
- Alert monitoring
- Backup verification
- Security patches
- Access review
- Incident analysis
- Vulnerability scans
- Performance review
- Policy compliance
- Security assessment
- Compliance audit
- Training updates

Security Implementation Success Story

"When we implemented our digital Wall of Fame, security was our top priority. Working with a vendor who understood FERPA requirements, we developed a comprehensive security framework that protects student privacy while celebrating achievements. Our system has operated for three years without security incidents, and regular audits confirm our compliance posture. The investment in security infrastructure has paid dividends in community trust and regulatory confidence."
Security Implementation Results:
- Zero Security Incidents: Three years of incident-free operation
- 100% Compliance: Passed all FERPA and state privacy audits
- Staff Confidence: 95% of staff comfortable with security procedures
- Community Trust: No privacy concerns raised by parents or alumni
- Response Readiness: Completed incident response exercises
- Monitoring Effectiveness: 99.9% system availability
- Training Success: 100% staff completion of security training
- Vendor Partnership: Strong security collaboration and support
This comprehensive approach to security demonstrates how proper planning enhances the overall community impact of digital recognition systems.
Future Security Considerations
Emerging Security Trends and Challenges
As technology evolves, new security considerations continue to emerge:
🤖 Artificial Intelligence Integration
- AI-powered content recommendations and privacy implications
- Automated threat detection and response systems
- Machine learning for user behavior analysis
- Data governance for AI training datasets
🔒 Enhanced Authentication
- Biometric authentication for sensitive system access
- Zero-trust security architectures
- Blockchain-based identity verification
- Passwordless authentication systems
⚠️ Evolving Threats
- AI-powered social engineering attacks
- Deepfake technology and content verification
- IoT device security vulnerabilities
- Supply chain security risks
📋 Regulatory Evolution
- Updated COPPA requirements for digital platforms
- State-level privacy legislation expansion
- International data transfer restrictions
- Sector-specific cybersecurity mandates
Staying ahead of these trends requires continuous engagement with security professionals and attention to emerging trends in digital recognition technology.
Budget Planning for Security Implementation
Security Investment Framework
| Security Component | Small District (1-5 schools) | Medium District (6-15 schools) | Large District (15+ schools) | Key Considerations |
|---|---|---|---|---|
| Security Assessment | $2,000-4,000 | $5,000-8,000 | $10,000-15,000 | Scope and complexity |
| System Hardening | $3,000-6,000 | $8,000-12,000 | $15,000-25,000 | Infrastructure requirements |
| Compliance Setup | $1,500-3,000 | $4,000-7,000 | $8,000-12,000 | Regulatory requirements |
| Monitoring Tools | $2,500-4,500 | $6,000-10,000 | $12,000-20,000 | Coverage and features |
| Staff Training | $1,000-2,000 | $3,000-5,000 | $6,000-10,000 | Staff size and complexity |
| Annual Maintenance | $2,000-4,000 | $5,000-8,000 | $10,000-15,000 | Support level required |
| Total Security Investment | $12,000-23,500 | $31,000-50,000 | $61,000-97,000 | Implementation approach |
Security ROI Calculation
Conclusion
Implementing robust security and data protection measures for digital Wall of Fame systems is not optional—it's essential for maintaining community trust, ensuring regulatory compliance, and protecting sensitive information. The comprehensive approach outlined in this guide provides educational institutions with the framework needed to secure their recognition systems while maximizing engagement and functionality.
<p>Security should be viewed as an enabler rather than a constraint, allowing schools to confidently showcase achievements while protecting privacy. By following established best practices, working with security-conscious vendors, and maintaining ongoing vigilance, institutions can create digital recognition platforms that serve their communities safely and effectively for years to come.</p>
<p>Remember that security is an ongoing process, not a one-time implementation. Regular assessment, continuous monitoring, and adaptive improvement ensure that your digital Wall of Fame remains protected against evolving threats while continuing to celebrate achievement and build community connections. For insights on how security considerations integrate with broader institutional goals, explore our article on <a href="/blog/roi-digital-alumni-recognition/">measuring the ROI of digital recognition systems</a>.</p>
<div class="cta-button mt-4">
<a href="https://rocketalumnisolutions.com/contact-us?utm_source=organic&utm_medium=seo&utm_content=walloffameus&utm_campaign=site-cta&utm_term=seo" target="_blank" rel="noopener" class="btn btn-primary btn-lg">Secure Your Digital Recognition System</a>
</div>
</div>
<div class="col-md-4">
<div class="security-checklist p-3">
<h4>Security Implementation Checklist</h4>
<div class="checklist-item mb-2">
✅ Conduct comprehensive risk assessment
</div>
<div class="checklist-item mb-2">
✅ Implement FERPA compliance measures
</div>
<div class="checklist-item mb-2">
✅ Deploy multi-layered security controls
</div>
<div class="checklist-item mb-2">
✅ Establish monitoring and incident response
</div>
<div class="checklist-item mb-2">
✅ Train staff on security procedures
</div>
<div class="checklist-item mb-2">
✅ Plan for ongoing security maintenance
</div>
</div>
</div>
Protecting student and alumni information while creating engaging digital recognition experiences requires careful planning and robust security implementation. Rocket Alumni Solutions specializes in secure digital Wall of Fame systems that meet the highest security standards while delivering exceptional user experiences. Our comprehensive approach to data protection ensures your institution can celebrate achievements confidently while maintaining full compliance with educational privacy regulations. Contact us today to learn how we can secure your digital recognition journey.
Live Example: Rocket Alumni Solutions Touchscreen Display
Interact with a live example (16:9 scaled 1920x1080 display). All content is automatically responsive to all screen sizes and orientations.